Free Cyber Risk Assessment
Assess Vendor Risk with the Power of Visibility
60% of all data breaches happen via third-parties. You have too much at stake to rely on a security score alone for vendor risk management. Soar to new heights in cybersecurity with the only security ratings platform built for third-party risk.
Cyber Risk Intelligence Beyond a Rating
Black Kite taps 1,000+ OSINT resources to provide multidimensional, standards-based insights that include:
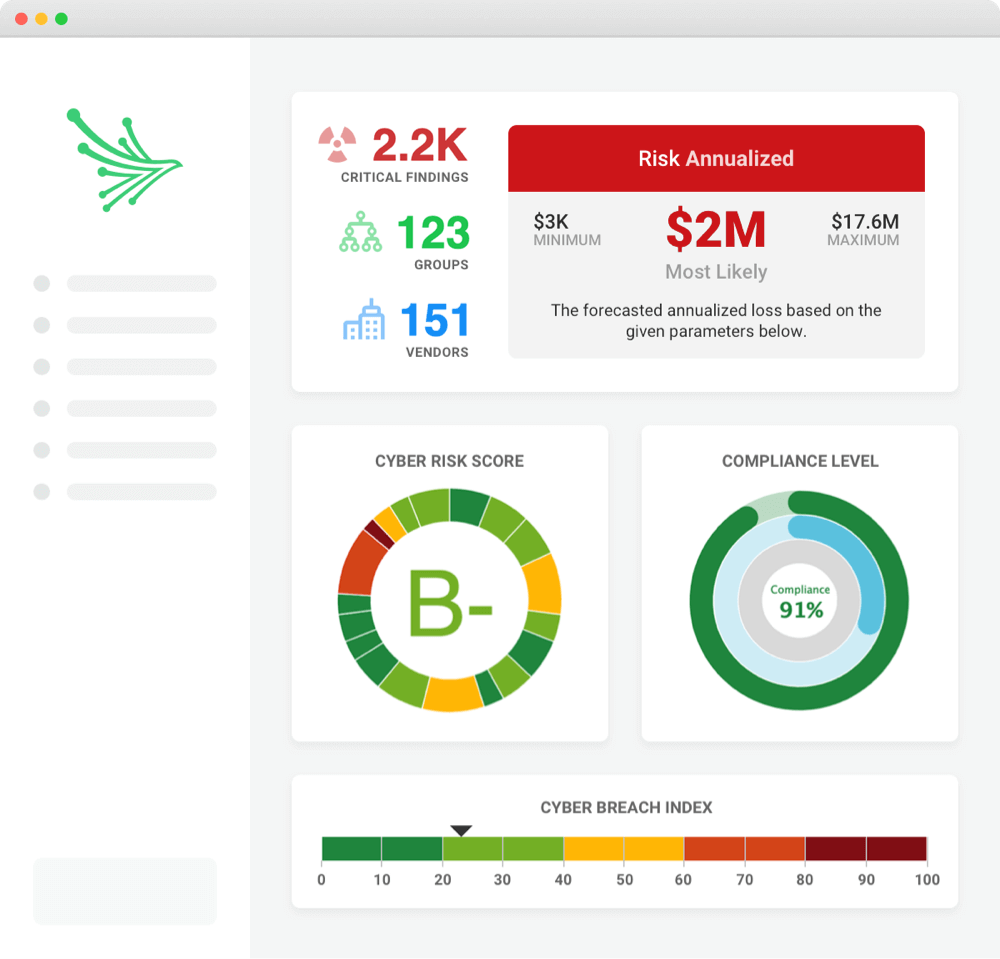
- Technical letter grades: Provides easy-to-understand ratings calculated using MITRE standards against 20 powerful, contextual categories.
- Financial impact analysis: Uses OpenFAIR™ to measure the probable financial impact in the event of a breach.
- Compliance ratings: Calculates the level of compliance with regulations such as CMMC, GDPR, PCI-DSS, HIPAA and more.
- Ransomware Susceptibility Index® ratings: Determines the probability of a ransomware attack against each vendor using key indicators and ransomware controls.
[Although we had an existing system for third-party risk assessments, it was a very manual process.] It took several man hours to review vendor responses, as well as several man hours for each vendor to complete assessments. That was effectively removed with Black Kite.
Regional Risk & Security Officer, $10-30B Food & Beverage Organization
