Lesson from TicketMaster Breach: CDN Security of third-party suppliers
UK-based company TicketMaster, a ticket sales and distribution company, experienced a major breach as they announced on June 27. Upto 40,000 UK citizens might have been affected while their customer information are compromised.
Many reports confirmed that TicketMaster was not directly breached or compromised, but a third-party supplier for their website was the one that is hacked. The third-party supplier, known as Inbenta, was a victim of a massive digital credit card-skimming campaign by the threat group Magecart affecting over 800 e-commerce sites around the world according to a recent article published by RiskIQ.
Recently, we have heard similar stories about breaches because of 3rd parties such as vendors, subsidiaries, web hosting companies, law firm partners, firms in supply chain, etc. Large companies such as financial institutions, e-commerce companies have been improving their cyber security system for external or even internal attacks. They can internally identify vulnerabilities of their own system by monitoring and/or scanning tools and take necessary precautions. However, all these efforts might be for nothing if 3rd party cyber risk is unknown. 3rd party risk management and data governance are growing concerns. More on 3rd-party risk management can be found here.
What really happened in TicketMaster Breach?
RiskIQ report sheds light on the breach and reports that hackers either replaced a javascript run for TicketMaster in Inbenta domains or injected malicious code into it to steal credentials. Using malicious Javascripts for hacking through code injections or XSS become quite popular in hacker society. Considering that 93.6% of all websites use Javascipts, it is no wonder that they are big part of attack surface.
RiskIQ article shows that hackers injected malicious code javascripts such as…
ticketmasteruk.inbenta.com/avatar/jsonp/inbenta.js
ticketmasteruk.inbenta.com/avatar/assets/js/inbenta.js
…which are hosted in subdomains used for TicketMaster.
Below are all the subdomains of Inbenta used for TicketMaster that are discovered by Black Kite Cyber Risk Score’s Digital Footpirint Asset Discovery Engine on June 28.
Was it something expected?
Detection of malicious JavaScripts is part of CDN (content delivery network) security. A content delivery network (CDN) is a large distributed system of servers deployed in multiple data centers across the Internet. Companies use CDNs for online libraries like JQuery. Detecting malicious code in JavaScripts is possible in your own systems with certain vulnerability scan tools on premise. However, detecting a CDN vulnerability at a third-party supplier’s system might be beyond the reach.
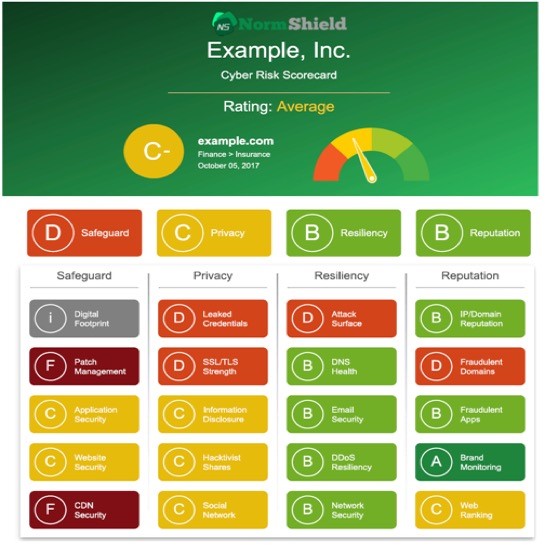
Fortunately, Black Kite analyzes the CDN content to detect possible vulnerabilities can be exploited for data breach like the one experienced by Inbenta. Any third-party company added to main company’s ecosystem is checked for such vulnerabilities in CDN security. Black Kite is currently only company that checks CDN security among security-rating service providers.
Black Kite provides easy-to-understand letter scores in the scale of A-F to better show a company’s cybersecurity posture. Our records showed that, even after the breach was announced (on June 28), the risk score of Inbenta for CDN Security is D showing some vulnerabilities such as XSS vulnerability. Even though company’s general security rating is good, the low score in CDN security is an indication of such possible attacks.
What does Black Kite offer?
This certain incident shows that assessing 3rd parties is quite important to avoid data breaches. Many companies either do not have any assessment on cyber risk of third parties or use old-school questionnaire methodology (sending a bunch of questions for third party to answer and assessing the risk based on the answer). Questionnaire-based assessment is very time consuming (even though there are some online tools for it) and answers are not reliable. There might be some cyber risks that are invisible to third party. This type of “hidden” risks can only be detected by gathering cyber threat intelligence and evaluating the risk.
Black Kite Cyber Risk Scorecard is a platforms that gather third party data and provide a risk score/security rating for companies related to a certain company. In Black Kite Cyber Risk Scorecard, a company can create an ecosystem that will includes the main company and all the third parties to be added. More than one ecosystem can be created such as an ecosystem including the companies/branches owned by the main company or an ecosystem for third-parties or you can even create an ecosystem which includes only law firms that you work with. Then, a third-party can easily be added by only typing its website.
Black Kite first discover the digital footprint of the third party (domains, subdomains, IP addresses, DNS Records, services, social media accounts, ASN, e-mails, company info, etc.) to see what hackers see on this third party. Then Black Kite evaluates the cyber risk by its proprietary algorithm on 20 different categories and how the cyber risk of this third party affects the overall ecosystem.
To learn your ecosystem risk scores in 20 different categories including CDN security, visit www.blackkite.com