Third Party Risk Intelligence
Built from a Hacker’s Perspective
It only takes 1 top-level domain (URL) to get started. Request Demo
360° View of Cyber Posture

Black Kite fills a fundamental security gap by making it simple for businesses to non-invasively quantify and monitor cyber risk across thousands of third parties. We provide intelligence from a technical, financial and compliance perspective: eliminating false positives and ensuring a holistic approach to vendor risk management.
Cyber Ratings Platform
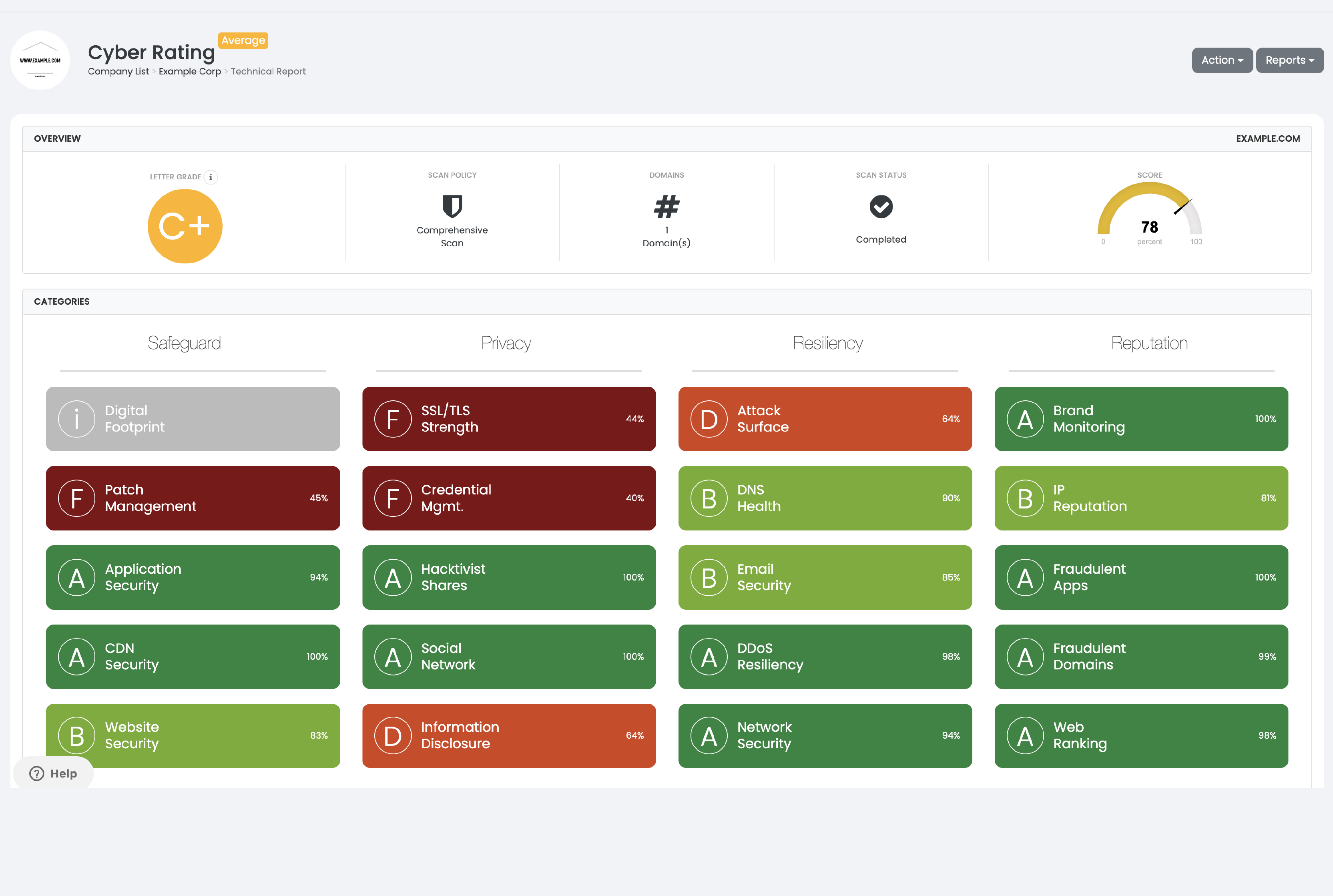
Technical Cyber Rating
Gain an easy-to-understand, trustworthy snapshot of your supply chain risk by visualizing defensible intelligence in the form of a letter grade. Black Kite utilizes industry-standard MITRE frameworks to convert technical data into digestible findings – allowing successful communication of risk to senior stakeholders.
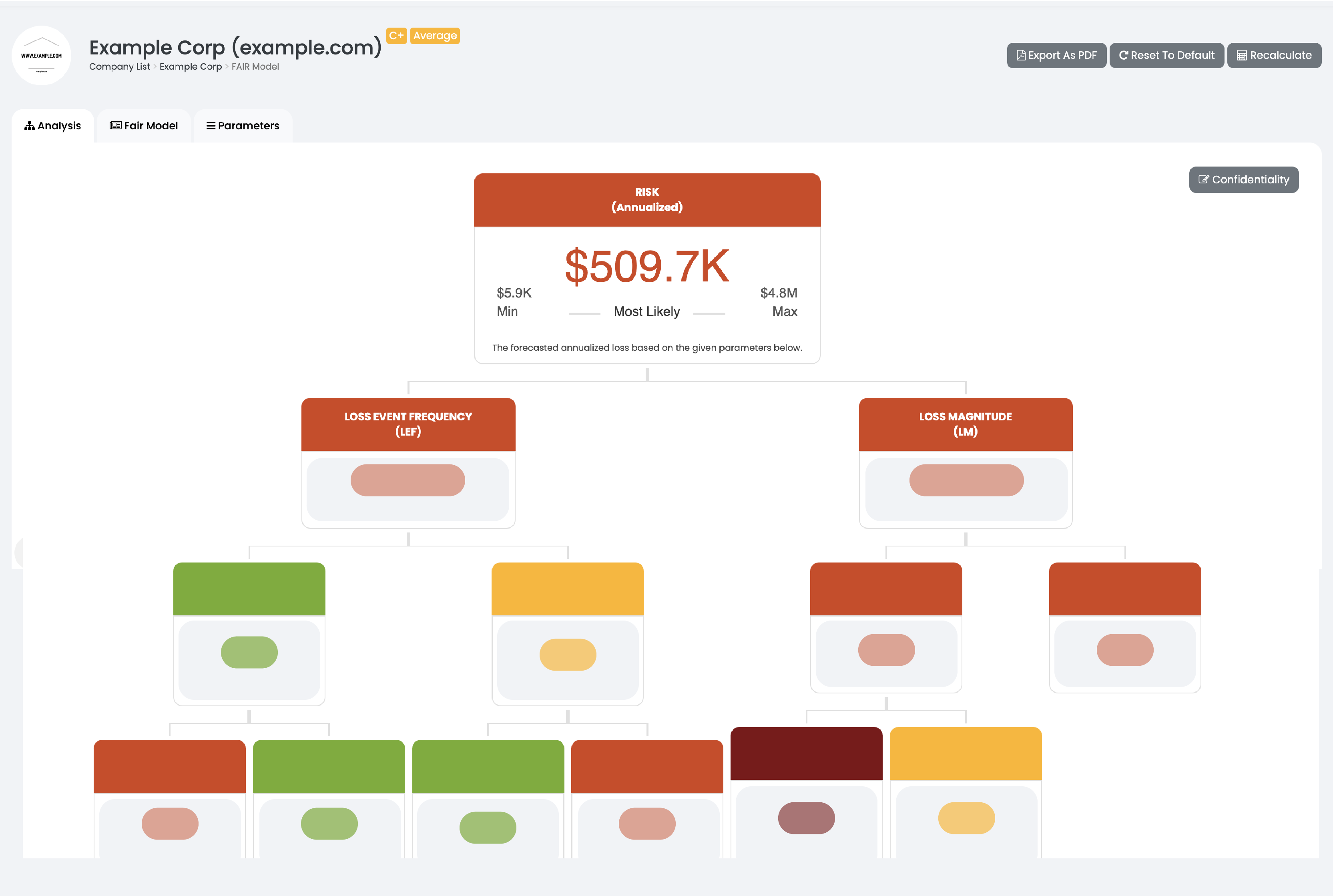
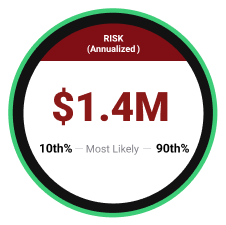
Risk Quantification
Black Kite uses the Open FAIR™ model to calculate the probable financial impact if a third-party vendor, partner, or supplier experiences a breach. Black Kite communicates this risk in quantitative, easy-to-understand business terms, facilitating a common language between IT and senior stakeholders.
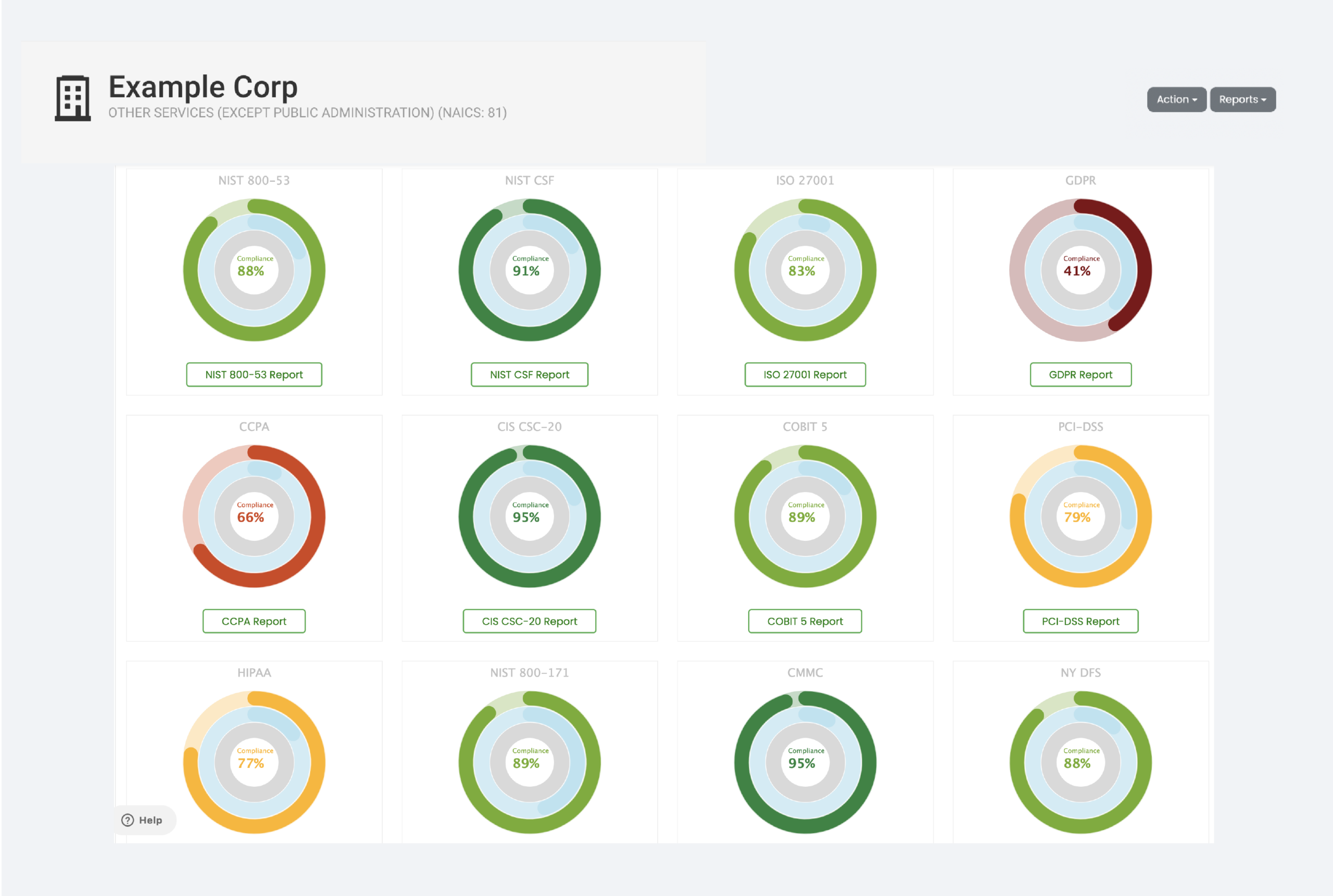
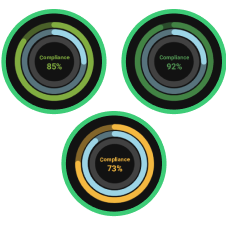
Compliance Correlation
Meet compliance requirements within hours, using automated parsing technology that maps to globally-recognized standards and frameworks with our UnIQue Parser. Additionally, the cross-correlation capability measures the external compliance level of a target company based on the standard input, saving time and effort for both you and your vendors.
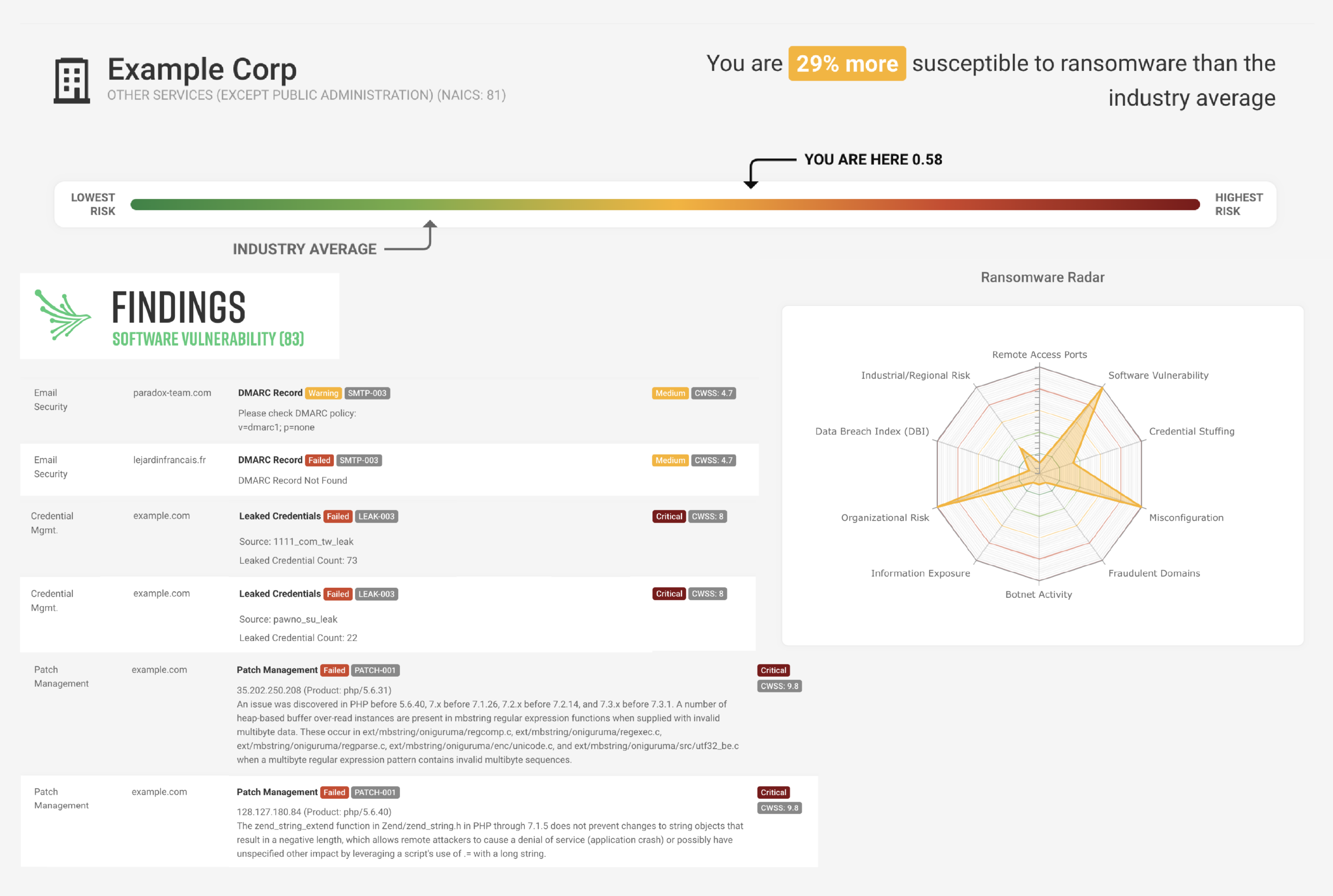
Ransomware susceptibility
The only cyber rating platform with a tool to detect the likelihood of a ransomware attack to your organization. The Ransomware Susceptibility Index® utilizes data analysis techniques and common indicators, including a third party’s location, industry, and annual revenue. By becoming aware of your risk, you can avoid business interruption and data loss by using our reliable data to develop informed policies around all emerging threats.
Where Insight Takes Flight™
360° Degree View of Cyber Risk
Providing intelligence from a technical, financial and compliance perspective, Black Kite eliminates false positives and ensures a holistic approach to vendor risk management.
Standards-Based Data
Black Kite is the world’s only fully transparent, standards-based cyber ratings platform, ensuring all users know exactly how their findings are calculated.
Unmatched Scalability
Engineering the largest data lake in the world, Black Kite provides you with visibility into over 34 million companies and counting, with 20+ risk categories and 290 controls – 3x the competition.
Powerful Performance behind 20 Categories
The total score is a weighted average of 20 category components,
providing unmatched breadth and insight into detected vulnerabilities.
Tap on items to learn more.
FocusTags™
Black Kite’s new tagging feature that automatically flags vendors who have experienced a data breach, ransomware attack or other significant cyber incident.
Within hours of an event, new tags are created for:
- Data breaches
- Ransomware attacks
- Geopolitical incidents, like the ongoing Russia-Ukraine conflict
- Software vulnerabilities
Black Kite vs. Competitors
Key players in the Security Rating Services (SRS) market (Black Kite, BitSight, SecurityScorecard, RiskRecon, and UpGuard) focus on publicly accessible, external data sources when performing vendor assessments. Although each player has a different approach, all providers in the SRS market use similar resources and techniques to collect data.
However, not all SRS providers are equal in terms of usability, analytics, compliance, technical depth, and threat intelligence capabilities. Compare Black Kite’s Cyber Risk Score with other SRS products in the market to help you make a better-informed decision.
Legend
-
Limited and Accurate
-
Limited
-
Partial
-
Complete/Available
-
Extensive
-
Not Available

Usability
Speed
Methodology
Compliance
Technical Depth
Threat Intelligence
ANALYTICS
Other
FREQUENTLY ASKED QUESTIONS
What is our Methodology?
What is Third-Party Risk Management?
How Does Black Kite Score Vendors?
Why is Continuous Monitoring Important?
Why Black Kite?
What is a Passive Scan?
Do I Need Permission to Scan a Vendor?
What Is the Cost?
Looks Great, How Do I Test Drive?
What is OSINT?
What is OPEN FAIR?
What Regulations and Frameworks Are Covered in the Compliance Module?
How Do You Validate Findings?
What Information Do You Provide to Improve My Vendor’s Score?


